CCoE Activities and Providing Google Cloud Security Preset Environments

Hello, Tada here from the Cloud Center of Excellence (CCoE) team in the KINTO Technologies Platform Group.
The CCoE team's mission is to make mobility product development more agile and secure by actively pursuing cloud-based system development and governance-based control.
CCoE at KINTO Technologies
CCoE activities
Based on the above mission, the CCoE team is pursuing numerous measures as an organization responsible for providing a broad range of support for making use of clouds and controlling the use of them. Let me tell you about some of the main ones.
Making use of clouds
In order to continuously support efficient development through knowledge sharing and HR development, we're pursuing the following:
- Cloud-related HR development
- Improve engineers' skills through study sessions and educational content that use KINTO Technologies' unique AWS skill map.
Controlling the use of clouds
In order to provide cloud environments that comply with group company security policies and to provide support to maintain security at all times, we're pursuing the following:
- Cloud security guidelines
- Pursue IaC development and security tools for compliance with security policies.
- Security preset cloud environments
- Provide cloud environments that are preconfigured in accordance with the above security guidelines.
Here's a simple picture of what we do. We provide cloud environments that are preconfigured mainly based on the cloud security guidelines, and get the development groups to make use of them. To keep these cloud environments secure, we monitor them using SIEM (Security Information and Event Management) and CSPM (Cloud Security Posture Management). We also use the security guidelines for HR development, information sharing sites, etc. Information about security gets updated daily, and cloud services are constantly evolving, too. So to keep up with these changes, we're aiming for sustainable activities with the guidelines at their core.
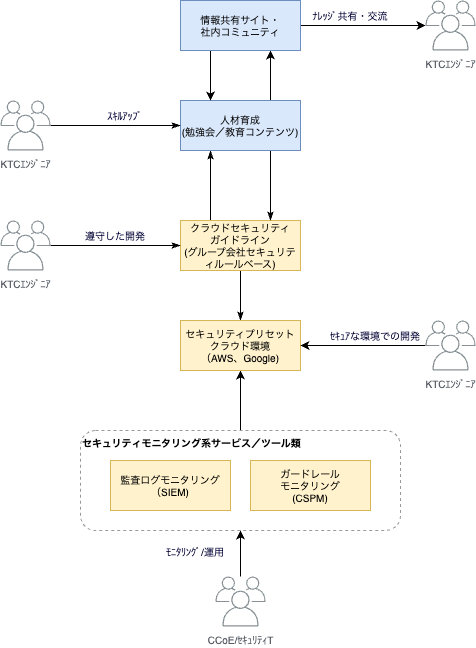
Now I'll tell you about something we're currently pursuing as a means of supporting controlling the use of clouds: security preset cloud environments (Google Cloud).
Working on creating security preset cloud environments (Google Cloud)
What are security preset cloud environments (Google Cloud)?
Security preset cloud environments are something we're developing as a way to encourage agile development by achieving both agility and security. Our company aims to let its development groups freely utilize cloud environments, so the idea is to impose the minimal restrictions needed to prevent undesirable uses.
So, what kinds of specific security do we set? Well, the following 2 security standards are our basic ones:
- CIS Benchmarks
- Group companies' security rules
And where do we set them? Well, the following 3 places:
- Organization policies
- Projects (Set when we create them)
- CSPM (Cloud Security Posture Management)
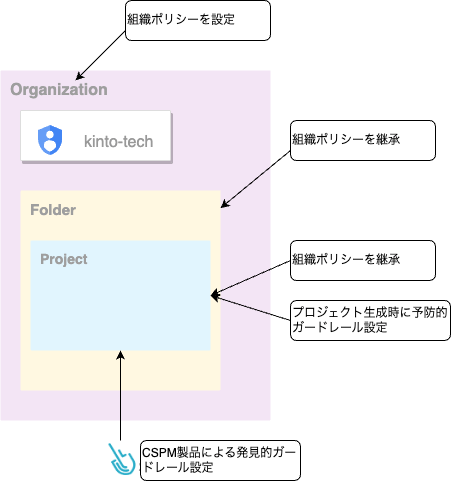
In the sections below, I'll give you the specifics about the security settings we use in each place.
What security have we set in organization policies?
We use organization policies to impose the minimal restrictions needed to prevent undesirable uses. This is the same as the concept called preventive guardrails. Preventive guardrails are a collective term for mechanisms and rules that prevent undesirable behavior and risks by providing preemptive constraints and restrictions on systems and processes. They can minimize the risk of security issues and compliance violations due to human error or unintentional acts. For the security preset cloud environments, we aim to keep restrictions to the minimum needed to prevent undesirable uses, so that they won't be too strict. We use the 2 security standards mentioned above as the basis for deciding what that minimum will be. Below are some organization policies we've actually put in place.
| Organization policy | Description | ---- | ---- | | constraints/GCP.resourceLocations | Limit the locations where resources can be created. Set multiple regions, including Asia. | | constraints/SQL.restrictPublicIp | Restrict public access to Cloud SQL instances. | | constraints/storage.publicAccessPrevention | Restrict public disclosure of data in Cloud Storage. | | constraints/compute.skipDefaultNetworkCreation | Restrict the creation of default networks and related resources when creating resources. | | constraints/iam.disableAuditLoggingExemption | Restrict principal exclusion settings from audit logs. |
These organization policies are set for organizations as a whole, and the same policies are inherited by folders and projects. If it so happens that they can't be accepted on the project side, the project-specific policy will override them.
What security have we set when creating projects?
We can't set them in an organization policy, but if we want to set rules that will function as preventive guardrails, we set them when creating projects. For example, in "2. Logging and Monitoring" in the CIS Benchmarks, there's a rule "2.13 Ensure Cloud Asset Inventory is Enabled" that we use to automatically activate the Cloud Asset Inventory when a project is created. Here are some of the other CIS Benchmark rules we set when creating projects.
| Item | Title | Description | | ---- | ---- | ---- | | 2.4 | Ensure Log Metric Filter and Alerts Exist for Project Ownership Assignments/Changes | Monitor and give alerts about project owner assignment. | | 2.5 | Ensure That the Log Metric Filter and Alerts Exist for Audit Configuration Changes | Monitor and give alerts about changes to audit settings. | | 2.6 | Ensure That the Log Metric Filter and Alerts Exist for Custom Role Changes | Project owners, organization role administrators, and IAM role administrators can create custom roles. Monitor and give alerts about creating custom roles, because they can end up with excessive permissions. | | 2.7 | Ensure That the Log Metric Filter and Alerts Exist for VPC Network Firewall Rule Changes | Monitor and give alerts about the creation or updating of firewall rules. | | 2.8 | Ensure That the Log Metric Filter and Alerts Exist for VPC Network Route Changes | Monitor and give alerts about VPC network route changes. | | 2.9 | Ensure That the Log Metric Filter and Alerts Exist for VPC Network Changes | Monitor and give alerts about VPC network changes. | | 2.10 | Ensure That the Log Metric Filter and Alerts Exist for Cloud Storage IAM Permission Changes | Monitor and give alerts about Cloud Storage IAM permission changes. | | 2.11 | Ensure That the Log Metric Filter and Alerts Exist for SQL Instance Configuration Changes | Monitor and give alerts about SQL instance configuration changes. |
Also, although we don't set the following CIS Benchmark rule when creating projects, we do set it for organizations as a whole:
| Item | Title | Description | | ---- | ---- | ---- | | 2.1 | Ensure That Cloud Audit Logging Is Configured Properly | Configure audit logging to track all activity and read and write access to user data. |
What security have we set via CSPM?
Now I'll explain the security we've achieved though CSPM (Cloud Security Posture Management). CSPM is used to detect and give alerts about risky operations in ways that can't be set when creating projects or in organization policies. This is the same as the concept of detective guardrails. Detective guardrails are mechanisms and rules for early detection of abnormal activity and security risks in systems and processes, and focus on detecting and analyzing incidents and abnormal activity. Preventive guardrails and detective guardrails play complementary roles. With our security preset cloud environments, based on the concept of detective guardrails, we're achieving risk detection and alerts using a CSPM product, but there were some twists and turns along the way when selecting which one to use.
Which CSPM product have we adopted?
Cloud Security Posture Management (CSPM) is a tool for the following: monitoring the security settings and configuration for the resources in cloud environments; and assessing and managing compliance with policies and guidelines based on best practice. Google Cloud has a service called Security Command Center, which has 2 tiers: Standard and Premium.
| | Standard | Premium | | ---- |:----:|:----:| | Security Health Analytics
(Including identifying critical configuration errors) | ○ | ○ | | Security Health Analytics
(PCI, CIS, compliance reports, etc.) | X | ○ | | Web Security Scanner | X | ○ | | Event Threat Detection | X | ○ | | Container Threat Detection | X | ○ | | Virtual Machine Threat Detection | X | ○ | | Rapid Vulnerability Detection | X | ○ | | Cost | Free | Subscription |
In our case, we wanted to achieve detective guardrails based on the CIS Benchmarks and other standards, so we opted to use Premium based on our requirements, but it's very costly and doesn't fit the current scale of our Google Cloud usage. For the CSPM product, we picked up a few candidates based on the points below, then conducted desk-checks and proof-of-concept tests.
- We can use the CIS Benchmarks and other compliance standards.
- We can also implement our own rules.
- It's cheap (compared to Security Command Center Premium).
The main products and evaluation comments are as follows:
- Forseti Security (Open-source security tools for GCP)
- Collects inventory information for Google Cloud resources and checks the auditing rules on a regular basis. The auditing rules available include IAM Policy, Bucket ACL, BigQuery Dataset ACL, and Cloud SQL Network. The CIS and other compliance standards can’t be used.
- Cloud Custodian (OSS)
- There's no default rule set for the CIS and other compliance standards, so we'd need to implement each rule from scratch.
- Third-party product (from Company S)
- The CIS and other compliance standards are prepared by default, and our own rules can also be implemented with Rego. It's a SaaS product, but is very cheap, and is available to buy from the marketplace.
Based on these findings, we decided to adopt the third-party product (from Company S). We vacillated over whether to go for Cloud Custodian, but decided in the end to prioritize speedy product integration and rule implementation. I'd like to write a blog article with more specifics on how we're using this product sometime, but for now, I'll just say that we're working to stay secure by introducing a CSPM product, detecting risky operations based on the CIS Benchmarks, etc., and continually making improvements.
:::message Actually, around February this year, it became possible to use Security Command Center Premium for individual projects rather than for whole organizations, making it easier to adopt in terms of cost as well. Premium has many other features besides CSPM, so I want to think about effective ways to juggle using it and the third-party product. :::
What are we doing about IAM permissions?
There's one more important thing I want to talk about: the issue of what to do about the IAM permissions for projects sent out to the development groups. In short, users are granted editor permissions. Of course, we're well aware that granting editor permissions is bad practice, but we do it as a trade-off between security and convenience for the development groups. So, we start with these permissions. Instead of this, we're moving toward thoroughly using the Policy Intelligence tools and operating under the principle of minimal permissions. I'd like to write a blog article on this as well sometime.
Summary
The following points give a summary of security preset cloud environments:
- They provide cloud environments that development groups can freely make use of, with only the minimal restrictions needed to prevent undesirable uses.
- They incorporate the concepts of preventive and detective guardrails.
- Preventive guardrails are achieved by using organization policies, and detective ones by using a CSPM product.
- In terms of IAM permissions, Policy Intelligence tools are used to thoroughly ensure that operations approach the principle of having the minimal permissions possible.
Future CCoE activities
Finally, I'd like to touch on our future CCoE activities. I talked about security preset environments for Google Cloud above, but we're preparing ones for AWS as well based on the same concepts. In addition, in order to keep the security preset environments secure, we're considering enhancing our security monitoring services and tools. I also talked a little about CSPM, but besides that, we're also working on developing other tools in an area called CNAPPs (Cloud Native Application Protection Platforms). Also, with the X.1060 framework gradually becoming more prominent these days, we plan to use it to continuously improve our organizational ability to respond to security issues. If I get the chance, I'd like to talk about this more as well sometime. Thank you for reading my article all the way to the end.
関連記事 | Related Posts
We are hiring!
【クラウドセキュリティエンジニア】SCoE G/東京・大阪
Security Center of Excellence ( SCoE ) グループについてマルチクラウド ( AWS, Google Cloud, Azure ) 環境のセキュリティガバナンスを担当しています。KINTOテクノロジーズ内だけでなく、グループ内の関連組織とも協力しながら、業務に行います。
セキュリティ/コーポレートエンジニア(オープンポジション)/IT/IS部/東京・名古屋・大阪
IT/IS部についてKINTOテクノロジーズという開発組織の「より開発に専念できる技術・セキュリティ環境」を創るため、2024年4月に新たに設立された部です。それぞれ専門領域を持った各組織が連携し、全社員に向けた価値を創出しています。
