情報セキュリティワークショップin越後湯沢2022 レポート

自己紹介
KINTOテクノロジーズにてCIO室セキュリティチームのチームリーダーを担当している森野です。
趣味は子ども時代を過ごした埼玉県大宮市(現さいたま市)のサッカーチームである大宮アルディージャの応援です。
最近は機動戦士ガンダム 水星の魔女にハマっていて毎週日曜日午後5時の放映を楽しみにしています。
本記事では先日初参加した情報セキュリティワークショップin越後湯沢2022のセッションの中から印象に残った講演を幾つか紹介させて頂きます。
情報セキュリティワークショップin越後湯沢とは
情報セキュリティワークショップin越後湯沢は1998年から年次で開催されている非常に歴史の長い情報セキュリティワークショップです。
2022年は10月7日(金)、10月8月(土)の2日間、デイタイムセッション会場は湯沢町公民館、デイタイムセッション中継・ナイトセッション会場は湯沢グランドホテルで行われました。


越後湯沢と言えばナイトセッション
越後湯沢の名物と言えば美味しい日本酒と温泉。。ではなくナイトセッションです。
例年チケット争奪戦が激しく、私もナイトセッションのチケットが取れず参加を諦めていましたが、幸いにも直前にチケットを譲ってくれる方が現れ参加することができました!
コロナ以前は講演者と参加者が車座となり議論を交わしていたそうですが、今年はコロナが収まっていないため講演者と参加者の距離を置いたセッションとなりました。
しかし、セッション中は参加者から講演者に対して活発に質疑応答が交わされていました。
帰ってきた!セキュリティのアレ in 越後湯沢
私も毎回配信を楽しみにしているポッドキャストセキュリティのアレを配信している方々によるナイトセッション。
- SBテクノロジー株式会社 プリンシパルセキュリティリサーチャー 辻 伸弘 氏
- インターネットイニシアティブ(IIJ) セキュリティ本部 セキュリティ情報統括室長 根岸 征史氏
- セキュリティインコ兼協力研究インコ piyokango 氏
piyokangoさんからは突然発生するサイバー攻撃に翻弄されないように天気予報のように攻撃を予兆することをやりたいというお話がありました。
汎用的なものは難しいかもしれませんが、例えばフィッシング犯罪はフィッシングサイトが実際に立ち上がる前にフィッシングサイトに使用するドメイン取得や証明書取得が行われます。
その活動を捕捉できればフィッシング犯罪の天気予報のようなことが行えるのではとお話を伺いながら思いました。
根岸さんからはCVSS(Common Vulnerability Scoring System)のスコアの高低だけで脆弱性対応の緊急度を判断するのではなく、実際にサイバー攻撃に使用されているのか否かを考慮するべきという問題提起がありました。
CVSSは名前の示す通り情報システムの脆弱性の深刻さを数値化する仕組みです。参考:IPA 共通脆弱性評価システムCVSS概説
日々、脆弱性情報を収集し自社システムへの影響を判断する者としては算出されたスコアから脆弱性対応の緊急度を計ることができるため大変便利です。
しかし、スコアが低いものでもサイバー攻撃に使用されることがあるため注意が必要とのことでした。
アメリカのCISA(CyberSecurity&Infrastructure Security Agency)がサイバー攻撃に使用された脆弱性を公開し随時更新しているので、このような情報を脆弱性対応の判断基準に加えることで、より安心・安全なシステムを提供できそうです。
辻さんは。。途中、他のセッションに参加したため聞き逃してしまいました。。辻さん、ごめんなさい。
フィッシングハンターもたまには温泉で休まナイト
日々フィッシングサイトと格闘している方々によるナイトセッション。
- 自称イケメンフィッシング詐欺ハンター にゃん☆たく 氏
- ozuma5119 氏
- KesagataMe 氏
- サイバー侍KAZUMI 氏
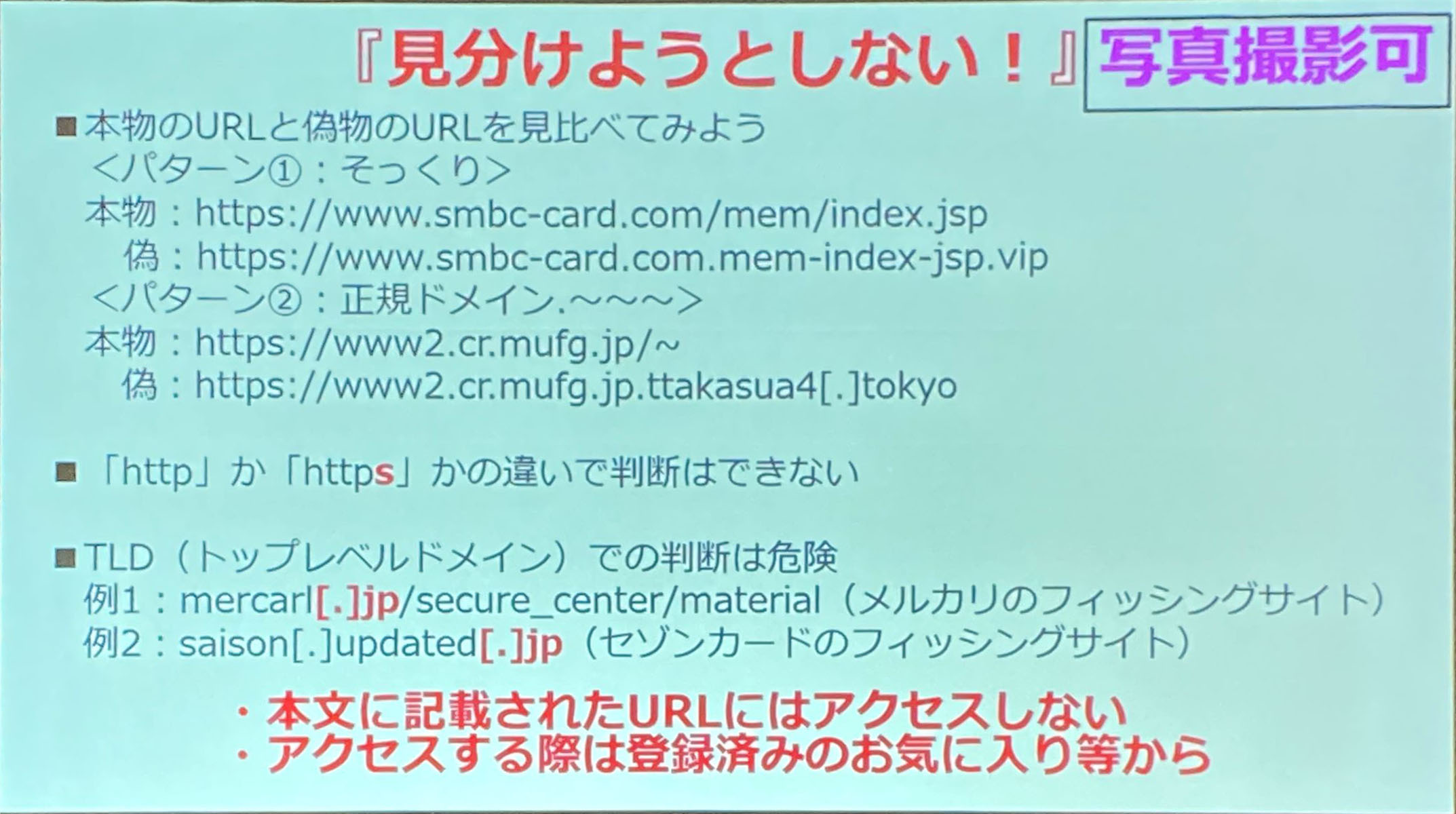
講演者の皆さんがフィッシングに引っかかる人が一人でも減るようにSNS等で拡散して欲しいと依頼されていたスライドをこのブログにも添付させて頂きました。
SMSやメールのリンクがフィッシングなのか否か判断することは非常に困難であるため、SMSやメールのリンクはクリックせず、ブラウザのブックマークや検索エンジンの検索結果から目的のサイトに移動しましょう。

若年層のネット活用の現状と、我々ができること
- 株式会社ラック サイバー・グリッド・ジャパン ICT利用環境啓発支援室 七條 麻衣子 氏
私には中学生の子どもがいるためとても興味深く講演を拝聴しました。
子ども達が専用のスマートフォンを持つ時期ですが9歳の時点で3割に達し13歳の時点では9割に達するそうです。私の想像より遥かに割合が高く驚きました。
若年層のネット活用の特徴について私の知らなかった点は以下の通りですが、共有に関して、スマートフォンアプリを使用してお互いの位置情報を共有するだけではなく、スマートフォンの電池残量まで共有していることには非常に驚きました。
- チャット・メッセージでの長文はNG
- 長文は画像で(メモ帳をスクショ)
- アカウントの使い分け
- 高校生の約半数がSNSでは実名登録(仮名だと友だちに見つけて貰えないため)
- 実況&動画で情報と時間の共有
お話を伺って理解できない使い方や危なっかしい使い方だと感じる点が多々ありました。しかし、理解できないと子どもに伝えるのは禁句で、それを伝えた瞬間に子どもは心を閉ざしてしまうそうです。理解はできなくてもありのままの現実を受け入れなさいとのことでした。
講演後に子どものSNSの使用について相談させて頂いたところ、危ないからといって禁止しても親に隠れて使用するだけで却って危険なため、親の監視の下、安全な使い方を教えながら使用させた方が良いとのアドバイスを頂きました。
脆弱性対応と情報共有~社内バグバウンティ制度の取り組みを通じて見えた事~
- エヌ・ティ・ティ・コミュニケーションズ株式会社 林 郁也 氏 / 塚越 さくら 氏
バグバウンティ制度とはソフトウエアの脆弱性を発見した方に対して報奨金を支払う制度のことです。
社外の方々に対してバグバウンティ制度を提供する場合、脆弱性を報告してくれた方が信頼できる方なのか否か判断することは非常に難しい問題です。
そこでエヌ・ティ・ティ・コミュニケーションズ株式会社では従業員を対象にバグバウンティ制度を提供することにしたそうです。従業員なら身元が確かなためです。
結果、ユーザの権限昇格が可能な深刻度の高い脆弱性が見つかるなど実際にシステムのセキュリティ強化に役立ったそうです。
副次的な成果として、自発的にグループが結成され勉強会が行われたり、エンジニア職以外から報奨金を得る方が現れるなど、従業員の新たな才能を発見する機会にもなったそうです。
当社でも社内バグバウンティ制度を取り入れてみたいなと感じました。
おわりに
日常業務から離れ様々な略歴を持った方々の講演を拝聴したり、ワークショップで出会った方々とお話させて頂いたことはとても刺激になりました。
記事の中で言及させて頂いた脆弱性対応の緊急度の判断方法はすぐにでも当社の業務に反映していきたいと考えています。社内バグバウンティ制度についてもすぐには難しいかもしれませんが当社にも導入できたら良いなと考えています。
越後湯沢以外にも温泉兄弟と呼ばれる兄弟ワークショップが各地で開催されています。皆さんも参加を検討してみては如何でしょうか。
サイバー防衛シンポジウム熱海
サイバー犯罪に関する白浜シンポジウム
サイバーセキュリティシンポジウム道後
九州サイバーセキュリティシンポジウム
関連記事 | Related Posts

Cybersecurity Symposium in Dogo 2023 Report

Participation Report of the 28th Shirahama Symposium on Cybercrime

情報セキュリティワークショップin越後湯沢2022 レポート

Introduction of Selective Disclosure JWT
![Cover Image for [Learning Roadside Station Podcast] Security & Privacy Study Session](/assets/blog/authors/aoi.nakanishi/2024-12-podcast/podcast_security.jpg)
[Learning Roadside Station Podcast] Security & Privacy Study Session

Behind the Scenes at Developers Summit 2024 KANSAI—Fresh Insights from Osaka Tech Lab ♪
We are hiring!
セキュリティエンジニア/サイバーセキュリティ G/東京・名古屋・大阪・福岡
セキュリティ・プライバシー部についてセキュリティチームは当社におけるセキュリティ専任組織として以下のような取り組みを行っております。
【Business Development】Business Development G/ Tokyo
About Business Development GroupThe Business Development G is involved in global projects in Full Service Lease of vehicles, the core of mo...

![[Mirror]不確実な事業環境を突破した、成長企業6社独自のエンジニアリング](/assets/banners/thumb1.png)

