私たちの脆弱性診断の取り組みについて

自己紹介
KINTOテクノロジーズにてCIO室セキュリティチームのチームリーダーを担当している森野です。
趣味は子ども時代を過ごした埼玉県大宮市(現さいたま市)のサッカーチームである大宮アルディージャの応援です。
本記事では脆弱性診断の主担当者であるヘビーメタル大好き中辻さんと共に私たちの脆弱性診断の取り組みについて紹介させて頂きます。
脆弱性とは
脆弱性とは何でしょうか。
脆弱性とはソフトウエアのバグ(欠陥、不具合)の内、情報セキュリティのCIAを損なうものを指します。
CIAは下記3つの単語の頭文字を取ったものです。
- Confidentiality(機密性)
- Integrity(完全性)
- Availability(可用性)
機密性とは情報に対して許可された者のみアクセス可能であることが保証されることを指します。
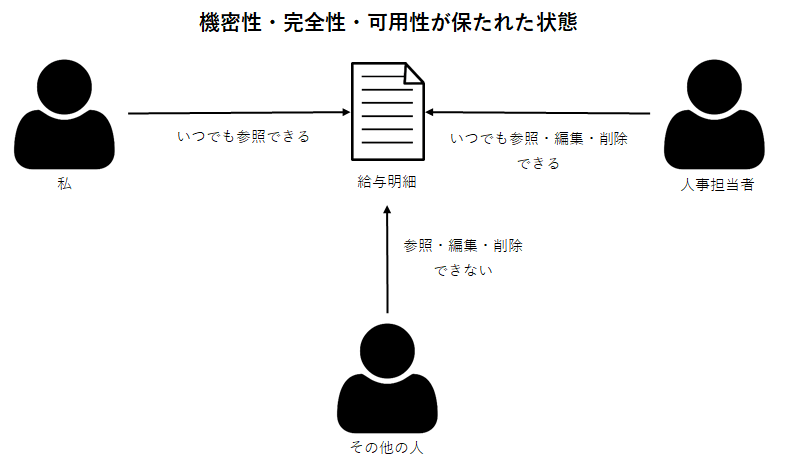
例えば給与明細参照用アプリがあったとして私の給与明細(情報)について会社の人事担当者と私(許可された者)のみアクセス可能である状態は機密性が保たれた状態です。
これがソフトウエアのバグにより私の給与明細に他人がアクセス可能である場合、機密性が損なわれた状態となります。
| 機密性が保たれた状態 | アクセス権を持っている人だけ給与明細にアクセス可能 |
| 機密性が損なわれた状態 | アクセス権を持っていない人も給与明細にアクセス可能 |
完全性とは情報に欠損や改ざんがなく完全に(正確に)保たれることが保証されることを指します。
前述の給与明細で例えると会社の人事担当者以外は私の給与明細の内容を消したり、書き換えたりできない状態は完全性が保たれた状態です。
私の給与明細を他人が消したり、書き換えたりすることが可能である場合、完全性が損なわれた状態となります。
| 完全性が保たれた状態 | 編集権限のある人だけ給与明細の削除、編集可能 |
| 完全性が損なわれた状態 | 編集権限のない人も給与明細の削除、編集可能 |
可用性とは必要な時にいつでも情報にアクセス可能であることが保証されることを指します。
人事担当者や私が必要な時にいつでも給与明細にアクセス可能である状態は可用性が保たれた状態です。
人事担当者や私が必要な時に給与明細にアクセスできない場合、可用性が損なわれた状態となります。
| 可用性が保たれた状態 | いつでも給与明細にアクセス可能 |
| 可用性が損なわれた状態 | 給与明細にアクセス不可 |
私たちが取り組んでいる脆弱性診断について
前述した情報セキュリティのCIAを損なうバグを検出することが脆弱性診断の目的です。
私たちの会社では以下のような脆弱性診断を実施しています。
- Webアプリケーション診断
- プラットフォーム診断
- スマートフォンアプリ診断
Webアプリケーション診断
Webアプリケーション診断には大きくわけて静的診断と動的診断があります。
静的診断はアプリケーションを実際に動かして診断するのではなくソースコードから安全ではないコードを発見する手法です。
動的診断は実際に動いているWebアプリケーションを診断する手法です。
いづれも自動診断と手動診断があります。
自動診断は設定に従ってプログラムがソースコード診断やWebアプリケーション診断を自動で実施します。
手動診断は人間がソースコード診断やWebアプリケーション診断を手動で実施します。
静的診断はSAST(Static Applilcation Secuirty Testing)、動的診断はDAST(Dynamic Application Security Testing)とも呼ばれます。
Webアプリケーション診断においてセキュリティチームは主に動的診断を担当していますので動的診断の自動診断と手動診断について説明します。
自動診断
私たちの会社では自動診断ツールにAppScanを使用しています。
例えばWebアプリケーションにSQLインジェクションの脆弱性があるのかないのか診断する場合、入力項目にSQLインジェクションを誘発する攻撃コードを入力、実行して診断します。
すべての入力項目に様々な攻撃コードを埋め込んでWebアプリケーションを診断するのは骨の折れる作業です。
診断中にWebアプリケーションのセッションが切れたらログインからやり直しです。画面遷移の順番が決まっている機能もあり、その画面遷移を繰り返し行うのも大変です。
自動診断ツールはそのような作業を自動化してくれるとても素敵なツールです。
手動診断
手動診断ツールはBurpSuiteを使用しています。
なぜ自動診断ツールがあるのに手動診断を行うのでしょうか。
セキュリティに関するコミュニティのOWASPは、セキュリティインシデントの発生原因をOWASP Top 10というランキング形式で公開しています。
OWASP Top 10の3位に入っているインジェクションは自動診断ツールが検出を得意とするものです。人間より自動診断ツールの方が様々な攻撃コードを漏れなく入力項目に入力(インジェクション)して診断できそうです。
では、1位のアクセス制御の不備はどうでしょうか。先程、例に挙げた給与明細参照用アプリの機密性が担保されているのか否かを診断するようなケースです。残念ながら自動診断ツールはWebアプリケーションの仕様を理解した上で、その挙動が適切か不適切かを判断するのは得意ではありません。このような種類の脆弱性は人手で診断を行います。
プラットフォーム診断
プラットフォーム診断はファイアウォールやロードバランサなどのネットワーク機器やWebアプリケーションが実行されているサーバの設定やサーバOSやミドルウエアの脆弱性を診断するものです。
プラットフォーム診断ツールはnmapを使用しています。
プラットフォーム診断では以下のような項目をチェックします。
・不要ポートの解放
・脆弱なソフトウエアの利用
・設定の不備
・プロトコル固有の脆弱性
参考:政府情報システムにおける脆弱性診断導入ガイドライン P.7
スマートフォンアプリ診断
スマートフォンアプリ診断は通常、アプリ部分の診断とWebAPI部分の診断があります。WebAPI部分はWebアプリケーションと同様の脆弱性診断を実施します。
アプリ部分はOWASPのOWASP Mobile Application Security Testing Guide (MASTG)を参考に静的診断を行っています。
アプリ部分の診断については今後、動的診断および静的診断に対応しているMobFSを活用することを検討しています。
脆弱性診断についてもっと学びたい人向けの書籍、資料、ウェブサイト
ここまで記事を読んで脆弱性診断についてもっと学びたい人もいらっしゃるのではないでしょうか。
そのような人向けに役に立つ書籍、資料、ウェブサイトを紹介します。
書籍
体系的に学ぶ 安全なWebアプリケーションの作り方 第2版 脆弱性が生まれる原理と対策の実践
通称、徳丸本と呼ばれている脆弱性診断について学ぶ人たちのバイブル的書籍です。鈍器に使えそうな分厚さなので持ち歩いて読みたい方は電子書籍版の購入をお勧めします。
資料
安全なウェブサイトの作り方
IPAが公開している名前の通り安全なウェブサイトの作り方に関する資料です。先程の徳丸本と比べてページ数少な目なので初めて脆弱性診断について学ぶ人はこちらから読み始めるのをお勧めします。
ウェブサイト
WebSecurityAcademy
前述した脆弱性診断ツールBurpSuiteの開発元であるPortSwigger社が運営している脆弱性の学習サイトです。
脆弱性に関するテキスト教材とハッキング演習から構成されています。
ブラウザ上で実際に手を動かしながら学習が可能です。
おわりに
この記事ではセキュリティチームの脆弱性診断の取り組みについて紹介させて頂きました。
最近WebAPIはREST APIではなくGraphQLによる実装が流行っています。
このようにITの世界は技術の流行り廃りが早いため、新しい技術で実装されたアプリケーションの脆弱性診断を適切に行えるよう日々情報収集および業務改善に努めたい行きたいと思います。
関連記事 | Related Posts

私たちの脆弱性診断の取り組みについて

Introducing VDP (Vulnerability Disclosure Program) Kaizen Activities

Reporting Back from the Sysdig Kraken Hunter Workshop

Hardening Designers Conference 2025 Event Report

Getting Started with Minimal CI/CD: Streamlining EOL and SBOM Management

Security as a Business Accelerator: How Our Security Organization Enables Speed × Quality
We are hiring!
セキュリティエンジニア/サイバーセキュリティ G/東京・名古屋・大阪・福岡
セキュリティ・プライバシー部についてセキュリティチームは当社におけるセキュリティ専任組織として以下のような取り組みを行っております。
ビジネスアナリスト(マーケティング/事業分析)/分析プロデュースG/東京・大阪・福岡
デジタル戦略部 分析プロデュースグループについて本グループは、『KINTO』において経営注力のもと立ち上げられた分析組織です。決まった正解が少ない環境の中で、「なぜ」を起点に事業と向き合い、分析を軸に意思決定を前に進める役割を担っています。

![[Mirror]不確実な事業環境を突破した、成長企業6社独自のエンジニアリング](/assets/banners/thumb1.png)

