Reporting Back from the Sysdig Kraken Hunter Workshop

Introduction
Hello! I'm Tanachu from the Security & Privacy Group at KINTO Technologies! I usually work on log monitoring and analysis using SIEM, building monitoring systems, and handling cloud security tasks as part of some projects in the SCoE group (here you can read aboutwhat's the SCoE group?) . Here is my self-introduction.
In this article, we share a report on our visit to the " Sysdig Kraken Hunter Workshop ," held on March 26, 2025, at the Collaboration Style event space near Nagoya Station.
 The Event Space
The Event Space
Using Sysdig Secure at KINTO Technologies
At KINTO Technologies, we mainly use Sysdig Secure for Cloud Security Posture Management (CSPM) and Cloud Detection and Response (CDR). I've put together more details in this blog, so feel free to take a look.
A Day in the Life of a KTC Cloud Security Engineer
What is the Sysdig Kraken Hunter Workshop?
Sysdig is a company founded by Loris Degioanni, the co-developer of the well-known network capture tool, Wireshark. It offers security solutions for cloud and container environments, built around Falco, an open-source standard for cloud-native threat detection developed by Sysdig. We use Sysdig Secure to monitor cloud activities such as permission settings and account or resource creation in cloud environment.
The Sysdig Kraken Hunter Workshop is a hands-on session where you run simulated attacks on a demo Amazon EKS environment. You go through a series of modules using Sysdig to practice detection, investigation, and response. If you pass the post-workshop exam, you'll earn a Kraken Hunter certification badge.
In this blog, I'll walk you through three modules that stood out the most.
Module 1: Simulated Attack and Event Investigation
In this module, we carried out a simulated attack on a demo Amazon Elastic Kubernetes Service (Amazon EKS) environment and used Sysdig Secure to detect and investigate the event.
First, following the provided documentation, we simulated a remote code execution (RCE) attack on the Amazon EKS demo environment. The simulated actions included:
- Reading, writing, and executing arbitrary files on the system
- Downloading files onto the system
After running the simulated attack, we accessed the Sysdig Secure console via browser. By checking the status of the targeted resources, we could confirm that Sysdig had detected events related to the attack.
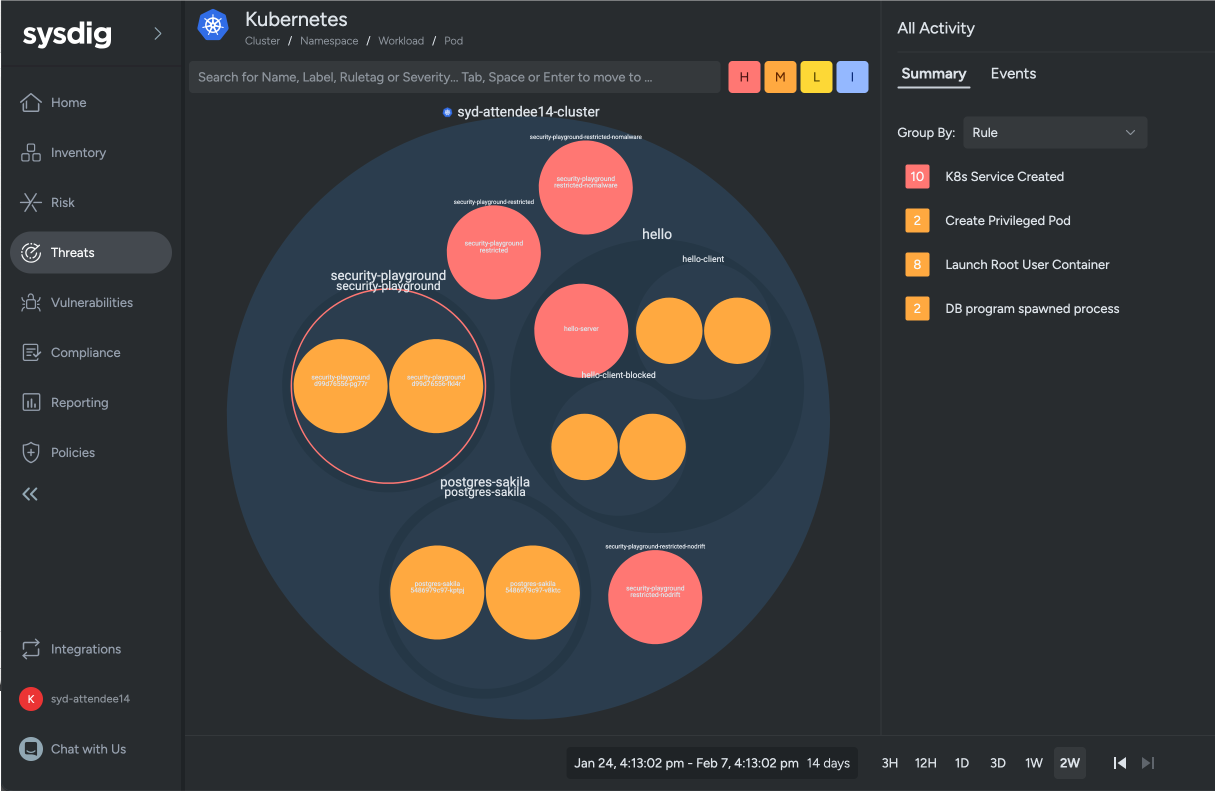 Reference: sysdig-aws workshop-instructions-JP
Reference: sysdig-aws workshop-instructions-JP
Digging deeper, we confirmed that Sysdig Secure had picked up the simulated attack in real time.
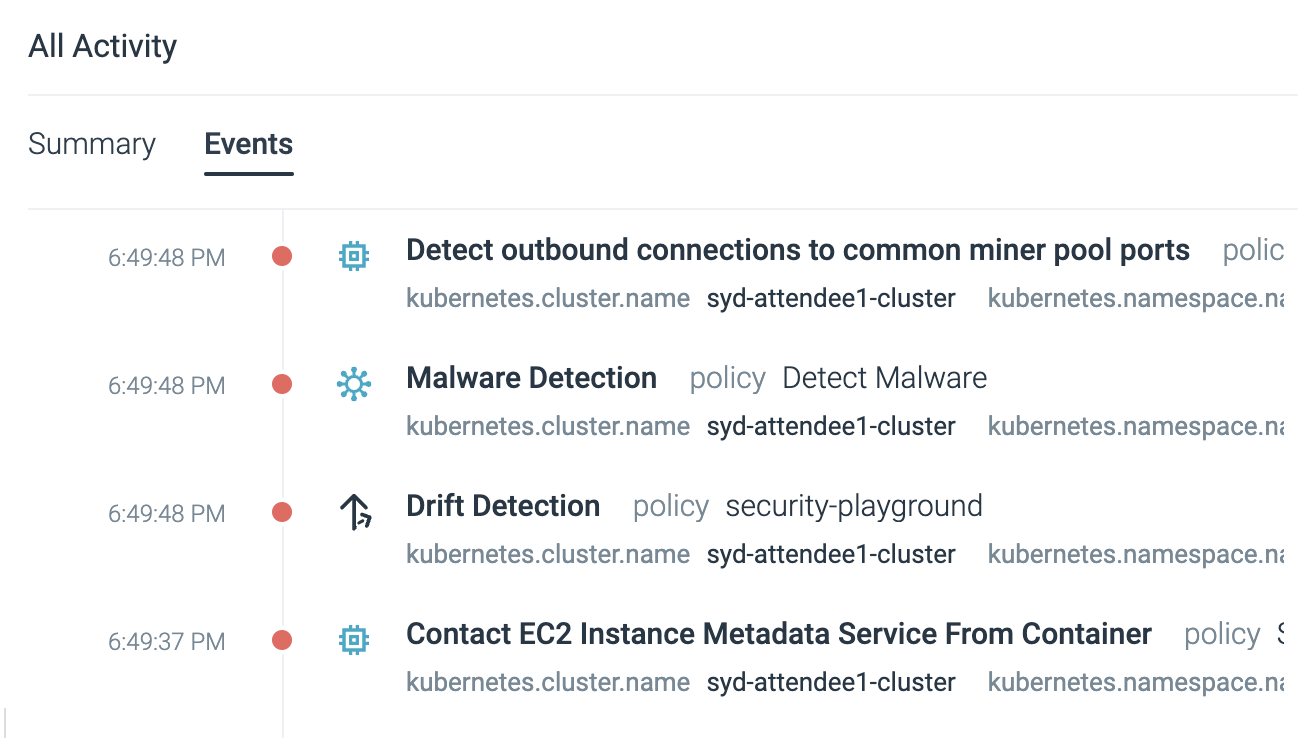 Reference: sysdig-aws workshop-instructions-JP
Reference: sysdig-aws workshop-instructions-JP
This hands-on flow let us try out a simulated attack and see exactly how Sysdig Secure handles detection and investigation through its console.
By running the attack myself and going through the investigation process with Sysdig Secure, I felt like I got a solid understanding of what the tool is capable of.
Module 2: Host and Container Vulnerability Management
In this module, we explored Sysdig Secure's features for managing vulnerabilities in both hosts and containers. Since our own products use containers and follow a microservices architecture, this topic is especially relevant to us.
Sysdig Secure offers several types of vulnerability scans: Runtime Vulnerability Scanning, Pipeline Vulnerability Scanning, and Registry Vulnerability Scanning.
The Runtime Vulnerability Scan lists all containers that have run in your monitored environment in the past 15 minutes, along with all hosts/nodes that have the Sysdig Secure Agent installed. Resources are automatically sorted by severity based on the number and risk level of vulnerabilities, making it easy to spot what needs your attention first.
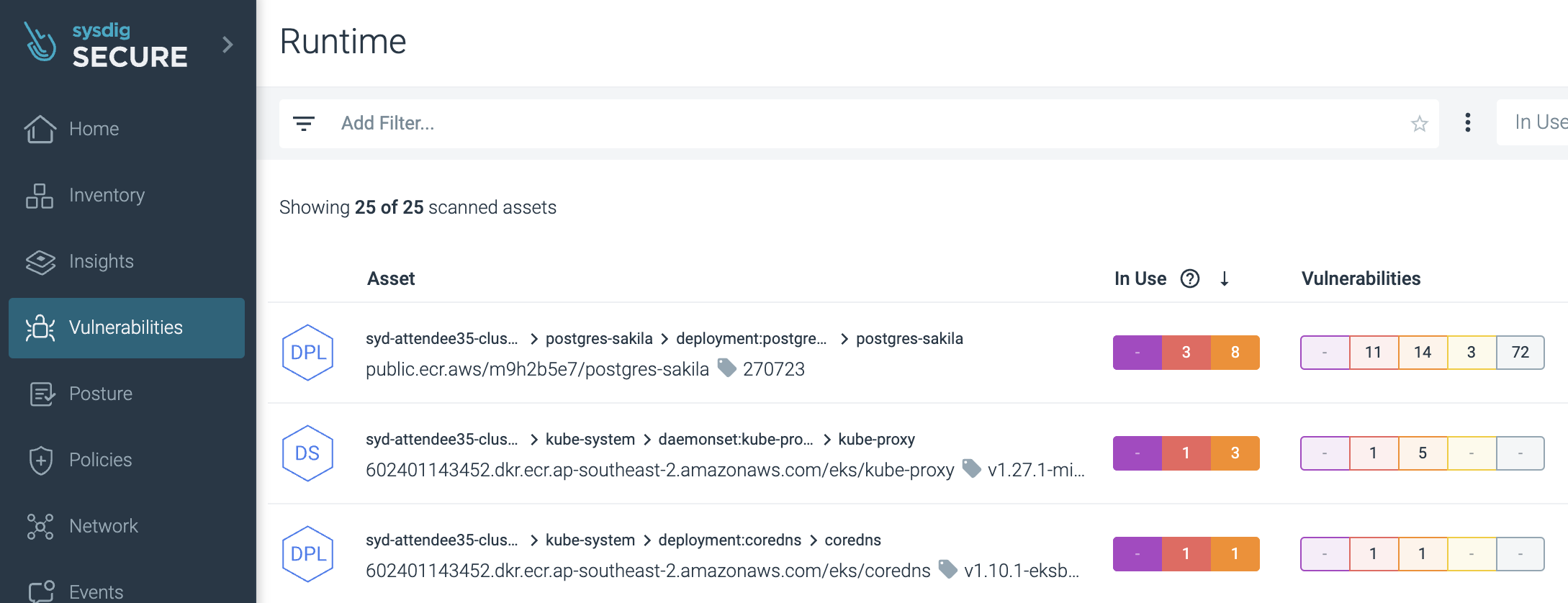 Reference: sysdig-aws workshop-instructions-JP
Reference: sysdig-aws workshop-instructions-JP
You can also click on any listed item to drill down and view vulnerability details.
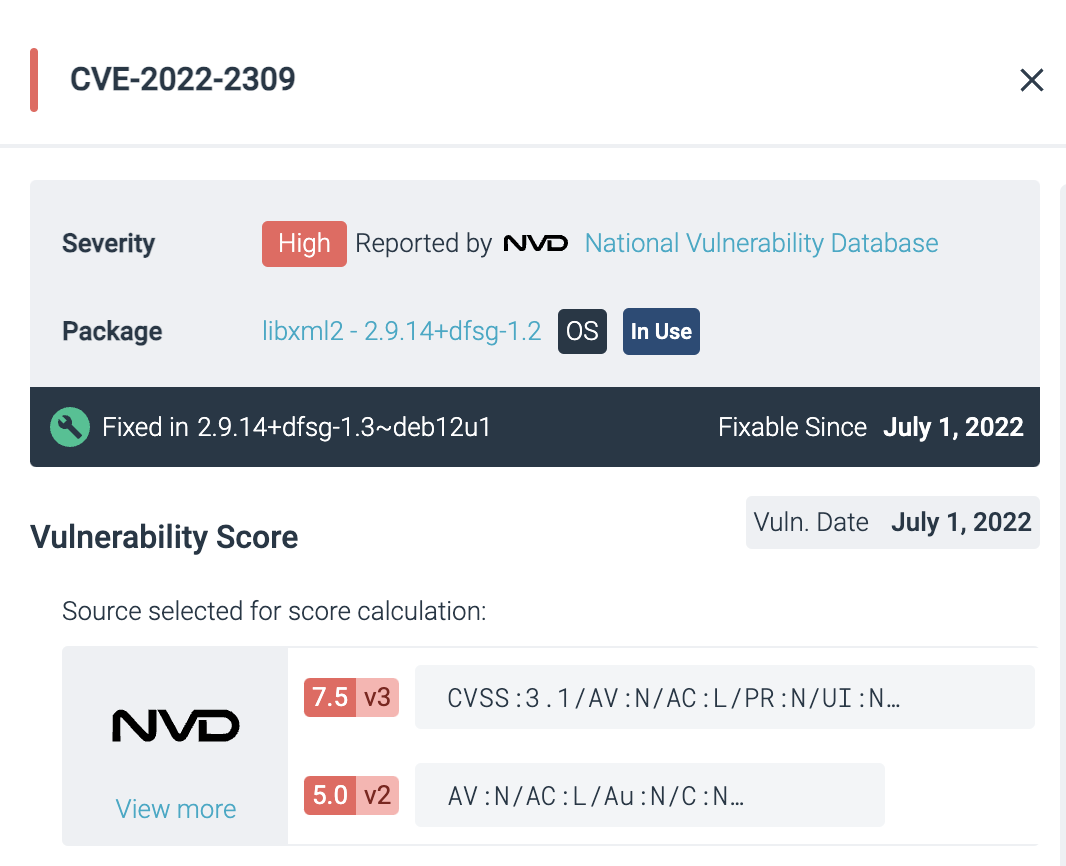 Reference: sysdig-aws workshop-instructions-JP
Reference: sysdig-aws workshop-instructions-JP
Pipeline Vulnerability Scan checks container images for vulnerabilities before they're pushed to a registry or deployed to a runtime environment. Registry Vulnerability Scan targets images already stored in your container registry. This way, you can check for vulnerabilities at each phase of the container image lifecycle, from development to production.
There are plenty of security tools out there for vulnerability management, but the Sysdig Secure console stood out to me for its sophisticated UI and intuitive usability.
Module 3: Container Posture & Compliance Management
In this module, we experienced how Sysdig Secure helps manage posture and compliance in cloud environments. As you may have probably seen or heard in the news, misconfigurations in the cloud are a major cause of security incidents. Since we build our products in a fully cloud-native setup, this isn't just others problem—it's something we take seriously. That's why this feature caught our attention.
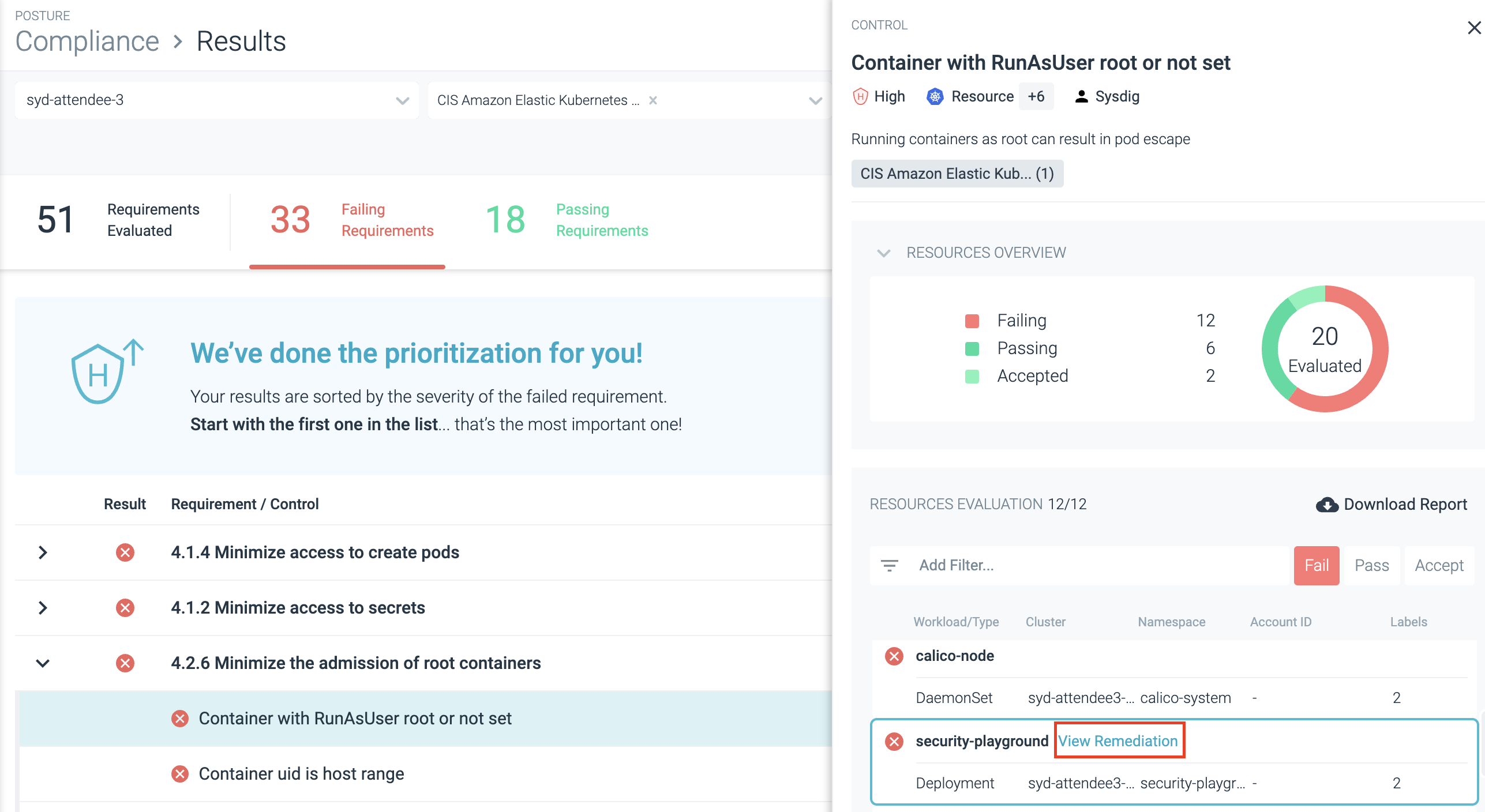
As a posture and compliance management feature, Sysdig Secure allows you to check if your environment complies with common standards like CIS, NIST, SOC 2, PCI DSS, and ISO 27001.
 Reference: sysdig-aws workshop-instructions-JP
Reference: sysdig-aws workshop-instructions-JP
It also highlights non-compliant resources and shows you how to fix them. While it's hard to say whether the steps will be practical in every situation, having that guidance readily available does save workloads on researching fixes. As an admin, that's a huge plus.
 Reference: sysdig-aws workshop-instructions-JP
Reference: sysdig-aws workshop-instructions-JP
Kraken Hunter Certification Exam
The Kraken Hunter certification exam had about 30 to 40 questions on a dedicated web page. The questions covered topics from the workshop, so if you paid attention, you had a solid shot at passing.
I struggled a bit with some of the finer details introduced at the start of the workshop, but I managed to pass the exam!
Here's the certification badge awarded to those who pass:
 Kraken Hunter Certification Badge
Kraken Hunter Certification Badge
Using Sysdig Secure Going Forward
We're exploring and pushing the following ways to get the most out of Sysdig Secure:
- CSPM: Creating custom policy rules in Rego based on our governance framework to ensure cloud security that aligns with our internal policies.
- CDR: Building custom rules using Falco to expand threat detection tailored to our environment.
- CWP: Testing and implementing Cloud Workload Protection (CWP) to secure our container workloads.
Summary
In the Sysdig Kraken Hunter workshop, we conducted a simulated attack against an Amazon EKS demo environment and got hands-on with Sysdig Secure—detection, investigation, response, and more.
Since we've only used a limited set of Sysdig Secure's features at our company, most of what was introduced was new to us. While we fumbled a bit at first, it was a great chance to see what the tool is truly capable of.
Joining the in-person workshop also gave us the chance to hear real stories from other companies—their challenges and efforts in the field. Big thanks to the organizers for making this happen.
Conclusion
Our Security and Privacy Group, along with the SCoE group who joined this workshop, are looking for new teammates. We welcome not only those with hands-on experience in cloud security but also those who may not have experience but have a keen interest in the field. Please feel free to contact us.
For more information, please check here.
関連記事 | Related Posts
We are hiring!
セキュリティエンジニア/サイバーセキュリティ G/東京・名古屋・大阪・福岡
募集ポジションについて本ポジションでは、セキュリティ・プライバシー部/サイバーセキュリティ グループに所属し、当社サービスおよび社内システムのサイバー防御強化に携わっていただきます。SOC運用や脆弱性管理を通じて、企業全体のセキュリティレベルを向上させる重要な役割を担うポジションです。
【クラウドエンジニア】Cloud Infrastructure G/東京・大阪・福岡
KINTO Tech BlogWantedlyストーリーCloud InfrastructureグループについてAWSを主としたクラウドインフラの設計、構築、運用を主に担当しています。

![[Mirror]不確実な事業環境を突破した、成長企業6社独自のエンジニアリング](/assets/banners/thumb1.png)

