ミニマルから始めるEOL/SBOM管理のCICDPipeline

こんにちは。プラットフォームGのPlatformEngneeringチームでPlatformEngineeringの考え方をベースにツール周りの開発・運用・展開の役割(とチームリーダーのようなことをしている、最近はスクラッチ開発側も担当するようになったんでスクラムとかプログラミング言語周りにひーひー言っている)島村です。
この記事は KINTOテクノロジーズアドベントカレンダー2024 の4日目の記事です🎅🎄
背景
SBOM(Software Bill of Materials)というものがあります。
2024年に経済産業省がセキュリティ対策に役立てましょうというのも言ってますし、2021年にアメリカでは標準で作ろうというお話にもなっております。とはいえ、そのために新しいSaaSとかOSSとか色々と導入するのはハードルが高い!と考えてしまうかもしれません。
KTCでは、OSSを活用してCICDのパイプラインに組み込んで、標準的にSBOMを作成して管理しています。
DevSecOpsの文脈で、SBOM作成に合わせて
- 脆弱性スキャン
- EOLの検査
も行っています。
「ミニマムスタート」と、その改善の事例としてご紹介します。
利点と欠点
何を使ってたっけ?が見えることが一番!
ちょっと前だと、log4jの脆弱性対応が記憶にあるとおもいます。弊社でも使ってないよね?という調査依頼が出されました。当時は設定ファイル見たりとか暫定の回避設定を共通で入れるように周知しましたが、今なら検索すれば一発でわかります。
- 利点
- 無料 でEOL/SBOM管理が始められる!👌
- 有償だとYamory(Cloudサービス)とかBlackDuckがあります
- SBOM生成だとMicrosoftが提供しているSBOM-TOOLもあります
- 有償ソフトウェアとかSaaSは申請とか諸々の手間が…
- 使っているツール群はGitHubActionsのActionとして準備されているので、使いやすい。
- ローカルでも動かせるので、色々とユースケースとして考えることができそう
- 無料 でEOL/SBOM管理が始められる!👌
- 欠点
- endoflifeなど有志に支えられているものが多いです
- xeol/syftともに開発が進んで頻繁にバージョンアップされていて、ファイルの不整合が起きることがたまに
ツール一覧
| 名称 | 機能 | 概要 |
|---|---|---|
| Syft | SBOM生成 | Anchoreが提供しているファイルやコンテナイメージからSBOMを生成するソフトウェア。SBOMの標準形式であるCycloneDXもSPDXも対応していますが、標準だとSyft独自形式になるのでご注意を。 KTCではCycloneDXのXMLで出力しています。JSONだとバージョン変わったりすると構成がかなり変わって取込時の考慮が増えるため |
| XEOL | EOLスキャナ | XEOLが提供しているEOLが含まれているかどうかを判断するスキャナ。内部構成はSyftをベースに、endoffile.dateの情報とマッチングをかけて判断している。主だった言語とOSは対応していることと、Issue上げたら結構早く修正してくれる感じがよいです。SaaSも提供していますが、今回はOSSを利用します。 |
| Trivy | 脆弱性スキャナ | aquaが提供している脆弱性スキャナ。AnchoreもGrypeという脆弱性スキャナを出しているので、Syftと組み合わせるならそっちが良いかと思いましたが、脆弱性検知をした際のCICD上の挙動がTrivyの方が好ましい(表示とか)と判断してこちらを。ファイル、リポジトリ、コンテナイメージ、SBOMからなどスキャンできる対象は多いので使える範囲は多いと思います。SBOMも生成できますが、XEOLの中身がSyftなので、相性を考慮して、今回は脆弱性スキャンだけ使います |
| GitHubActions | CICDツール | GitHubに包含されているCICDツール。KINTOテクノロジーズではGitHubActionsを使用してアプリケーションのビルド・リリースなどを実行しています。SBOM管理では、コンテナ作成タイミングのワークフローにSBOM生成を組み込んでいます。 |
| CMDB(内製) | CMDB | Configuration Management Database。構成管理のデータベースのこと。リッチな機能までは不要でしたので、KINTOテクノロジーズではCMDBを内製しています。最近はリポジトリ情報管理、EOL情報やSBOMのパッケージも取り込んで検索できるように機能追加されました。 |
ワークフロー概要図
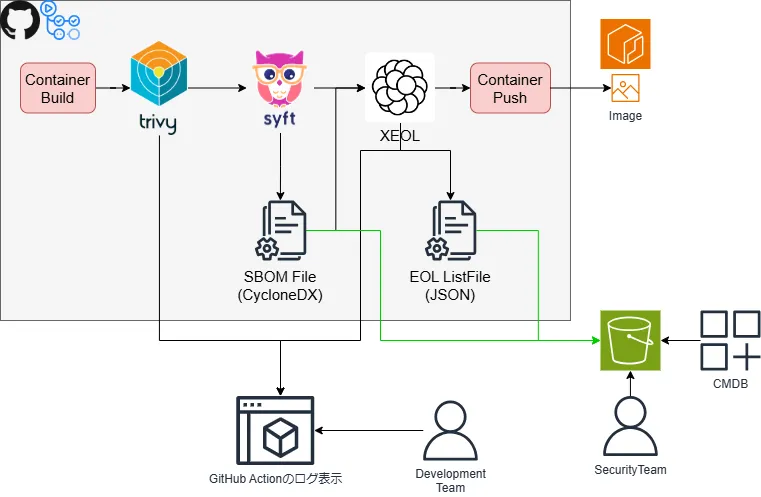
パイプライン抜粋(GitHubActions)
基本的にはアプリケーションビルドではなくShipのタイミングで実施しましょう。
SBOMファイルはバージョン管理をしてもよかったんですが、最新のみで問題はないかなと考えて、上書きするようにしています。ビルドに組み込むと、実際にワークロードにあるコンテナのSBOMじゃないものになるので、注意が必要です。
パイプラインでXEOLを2回呼び出しているのは、GitHubActionへのログ表示とファイル生成のためです。モードが別のようで、一括でやってくれなかったんで、分離することになりました。
## Trivyでの脆弱性診断
- name: Run Trivy vulnerability scanner
uses: aquasecurity/trivy-action@master
with:
image-ref: '${{ ImageName }}:${{ IMAGETAG }}'
format: 'table'
exit-code: '0' ## 脆弱性があってもImageBuild/Pushをする場合はここを「0」にする
ignore-unfixed: false
vuln-type: 'os' ## Javaなども含みたい場合は「library」を追加する
severity: 'CRITICAL,HIGH'
## SYFTでのSBOM作成
- name: Run Syft make sbom files(format cyclone-dx)
uses: anchore/sbom-action@v0
with:
image: '${{ ImageName }}:${{ IMAGETAG }}'
format: cyclonedx
artifact-name: "${{ github.event.repository.name }}-sbom.cyclonedx.xml"
output-file: "${{ github.event.repository.name }}-sbom.cyclonedx.xml"
upload-artifact-retention: 5 ## Artifactの有効期限
## XEOLでのSBOMからのEOLライブラリ検知(WF中での表示)とファイル作成
- name: Run XEOL mw/sw EOL scanner from sbom file
uses: noqcks/xeol-action@v1.1.1
with:
sbom: "${{ github.event.repository.name }}-sbom.cyclonedx.xml"
output-format: table
fail-build: false
- name: Run XEOL mw/sw EOL scanner from sbom file and Output file
uses: noqcks/xeol-action@v1.1.1
id: xeol
with:
sbom: "${{ github.event.repository.name }}-sbom.cyclonedx.xml"
output-format: json
fail-build: false
## AWSのクレデンシャルの設定(SBOM)
- name: AWSクレデンシャル
uses: aws-actions/configure-aws-credentials@v4
with:
role-to-assume: ${{ S3_ACCOUNT_ROLE }}
aws-region: ${{ AWS_REGION }}
## SBOM/EOLを管理するTeamのS3Bucketに保存する
## イメージ名やリポジトリ名でS3の中で階層分けをするので、Cutで抽出。
- name: SBOM and EOL file sync to s3 bucket
run: |
ECRREPOS=`echo ${{ ImageName }} | cut -d "/" -f 2,3`
echo $ECRREPOS
aws s3 cp ${{ github.event.repository.name }}-sbom.cyclonedx.xml s3://${{ s3-bucket-name }}/${{ github.event.repository.name }}/$ECRREPOS/sbom-cyclonedx.xml
aws s3 cp ${{ steps.xeol.outputs.report }} s3://${{ s3-bucket-name }}/${{ github.event.repository.name }}/$ECRREPOS/eol-result.json
改善されたことと今後
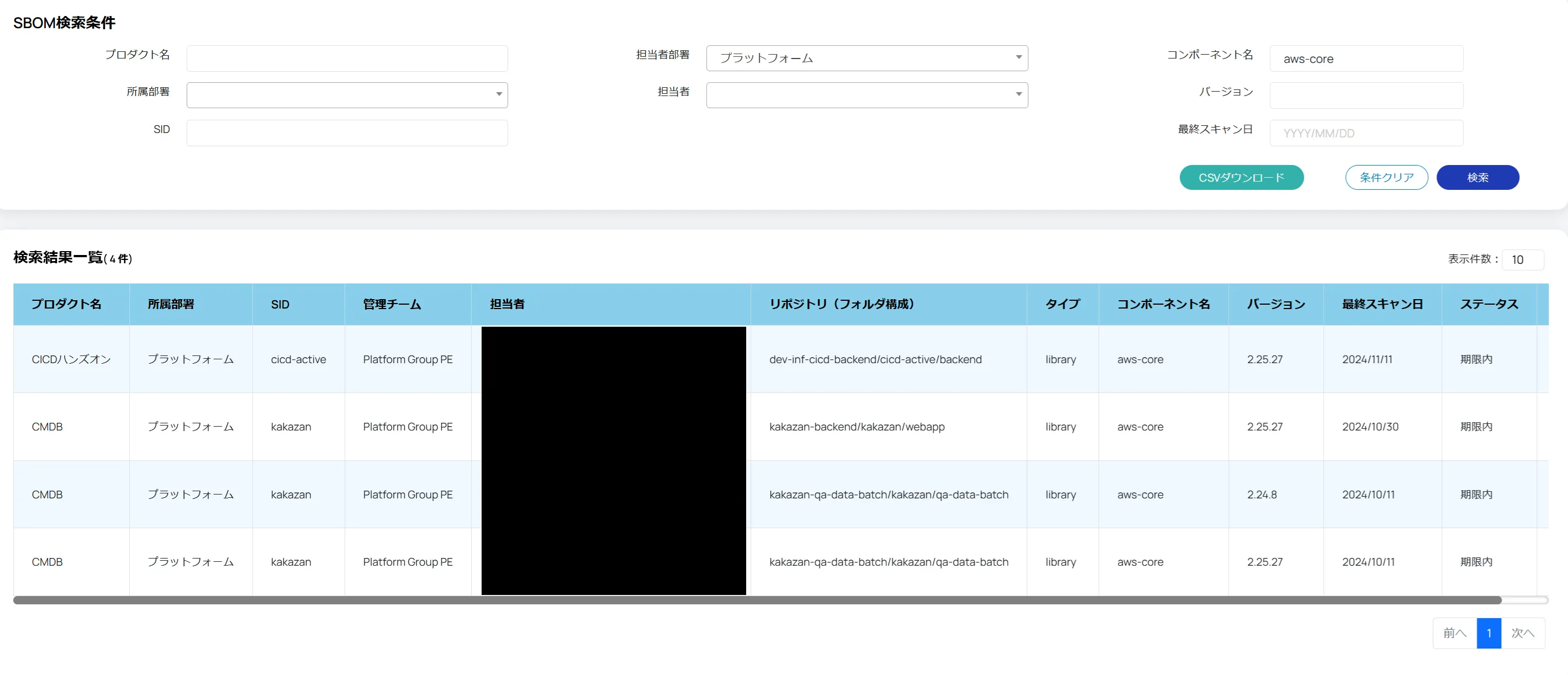
自分の部署で、AWS-COREのライブラリを使っているかどうかを確認した結果
自分の部署で、EOLがあるかどうかを確認した結果
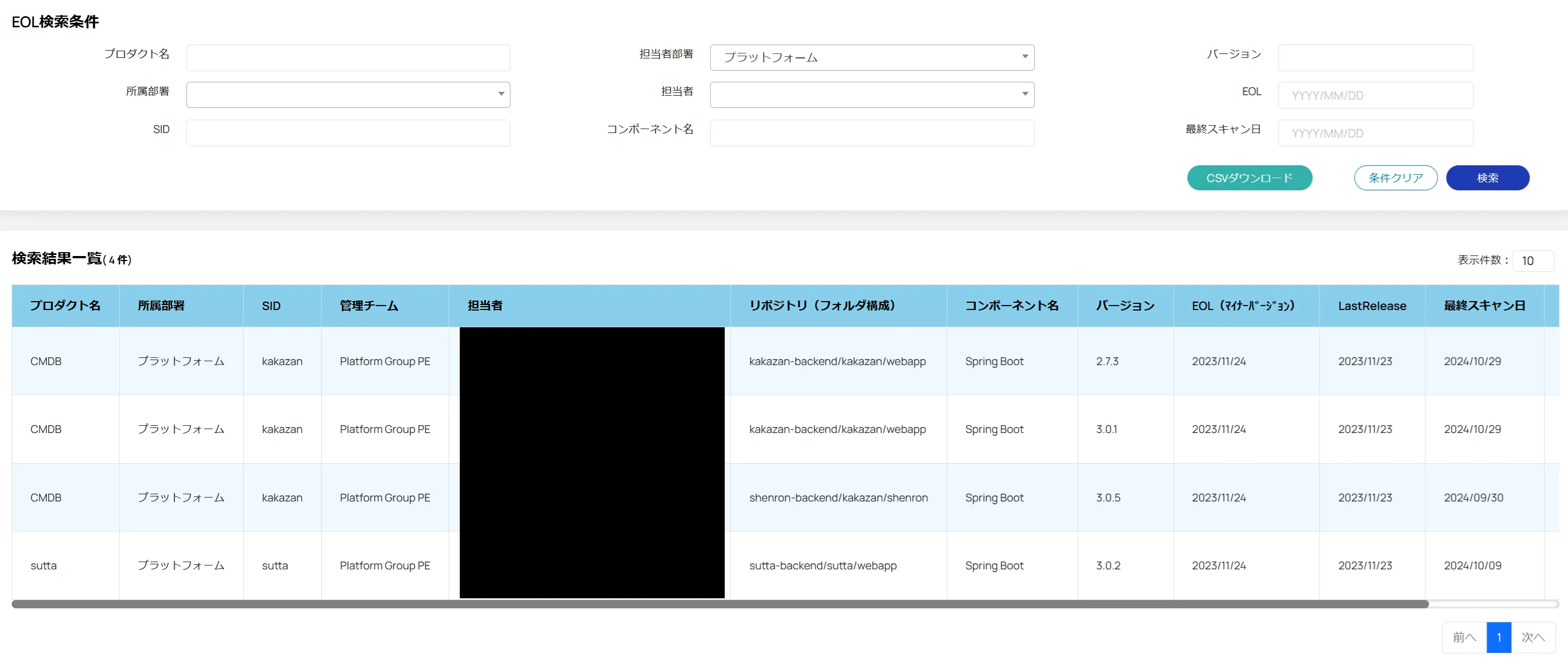
KTCではCMDBへSBOM/EOLの一覧を取り込んだため、
- 自身のプロダクトに何のライブラリが使われているか?
- EOLになっているものはないか?
が上記の通り、検索して確認できるようになりました。内製CMDBでは直近でEOLになるライブラリ・パッケージも出してくれるので、事前対応も容易です。
SBOM管理の第一歩は、SBOMファイルなどをJSONで出力して、jqで成形してエクセル管理でもいいと思います。
今後は、定期的にEOLを含んだプロダクトへ、チケットで対応依頼を行う運用を開始したいと考えています。
セキュリティチームとか色々と巻き込んでいくつもりです。
所感
EOL管理周りのツールは調べましたが多くはなく、SBOM管理とかソフトウェア管理、資産管理の延長として提供しているものが多い印象です。
OSSやライブラリを使った開発も多いので、EOLを定期的に見れる改善は脆弱性対策としてもかなり有用かと感じています。ライブラリも1年~2年でEOLとなって、バージョンの追従をする必要が多いと思いますし。
見えるというのは、"気付かない"・"見なかったことに"という対策には良いと思いますので、O11yと同じでまずは「みえる」を目標にしましょう。
実際には、修正依頼も含めた運用まで建付けないと、実効性はないのかもしれません。
が、「ミニマルから始める」と題して、まずは作ろう!始めよう!ということで、今回の記事を書きました。
さいごに
PlatformEngneeringチームは、社内向けの横断ツールを統制して必要なものを開発しています。
Platformグループの他チームが作ったものを受け入れたり、必要なものを新規作成や既存のものをマイグレーションしたりしています。MSPチームの定例作業の自動化とか、CDKにも手を出そうとしてるので、ManagedService以外にもプログラミングも行い始めました。
こういった活動に少しでも興味を持ったり話を聞いてみたいと思った方は、お気軽にご連絡いただければと思います。
関連記事 | Related Posts

ミニマルから始めるEOL/SBOM管理のCICDPipeline
Achieving Auto Provisioning in ECS Environments

How We Reduced AWS Costs by 65%—and What We Discovered Beyond That

Advent Calendar 2023 Announcement
Getting Started with Prometheus, Grafana, and X-Ray for Observability (O11y)

Half-Year Anniversary of the Launch of KINTO FACTORY: A Path of Challenge and Learning
We are hiring!
【クラウドエンジニア】Cloud Infrastructure G/東京・大阪・福岡
KINTO Tech BlogWantedlyストーリーCloud InfrastructureグループについてAWSを主としたクラウドインフラの設計、構築、運用を主に担当しています。
シニア/フロントエンドエンジニア(React/Typescript)/KINTO中古車開発G/東京・大阪・福岡
KINTO開発部KINTO中古車開発グループについて◉KINTO開発部 :66名 KINTO中古車開発G:9名★ KINTOプロダクトマネジメントG:3名 KINTOバックエンド開発G:16名 契約管理開発G :9名 KINTO開発推進G:8名 KINTOフロントエンド開発G...

![[Mirror]不確実な事業環境を突破した、成長企業6社独自のエンジニアリング](/assets/banners/thumb1.png)

