Introducing VDP (Vulnerability Disclosure Program) Kaizen Activities

Self-Introduction
My name is Morino, and I work at KINTO Technologies, mainly in product security and security governance. I'm a fan of RB Omiya Ardija and Chiikawa. For the past 10 years, I've been involved in cybersecurity and information security. Prior to that, I spent many years as a web application engineer, focusing on the development and operation of web performance measurement systems and front-end platforms for e-commerce sites. In this article, I’d like to share our Kaizen efforts related to the Vulnerability Disclosure Program (VDP).
What is the Vulnerability Disclosure Program (VDP)?
The VDP is a system that enables companies and organizations to receive vulnerability reports from external security researchers and white hat hackers. Public awareness grew in October 2023 when Rakuten Group placed a "security.txt" on a public server and launched its VDP.
Reference: Rakuten places text on public server — "security.txt" to help improve security (in Japanese)
What is security.txt?
Published as RFC 9116 in April 2022, security.txt: A File Format to Aid in Security Vulnerability Disclosure helps standardize how companies and organizations share vulnerability reporting information, making it easier for security researchers to report issues. We also published our own security.txt in November 2023.

Reactions After Installing security.txt
Most inquiries were about whether we offer rewards (we don't), and many reports didn't clearly indicate whether they actually involved vulnerabilities in KINTO/KTC.
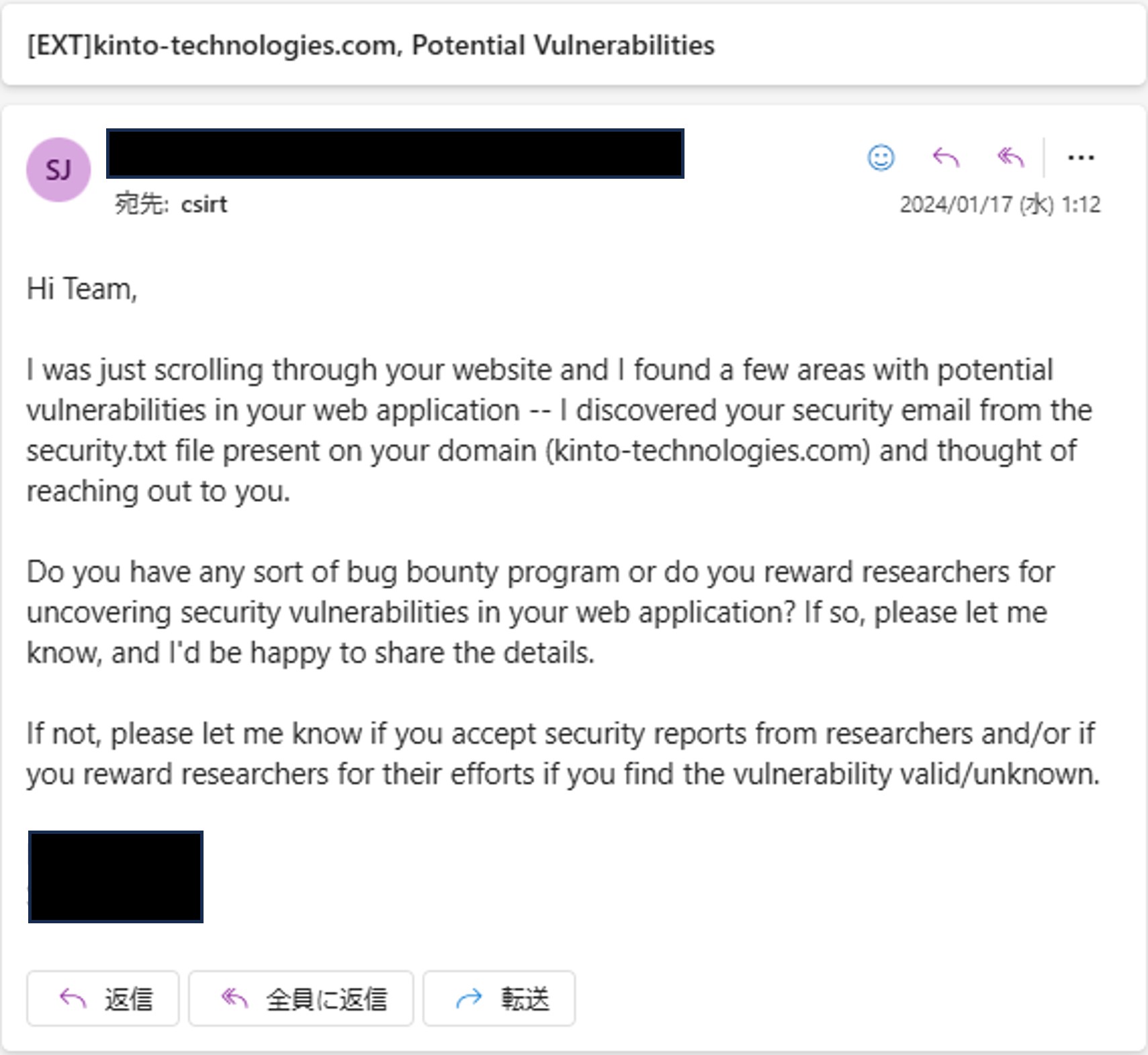
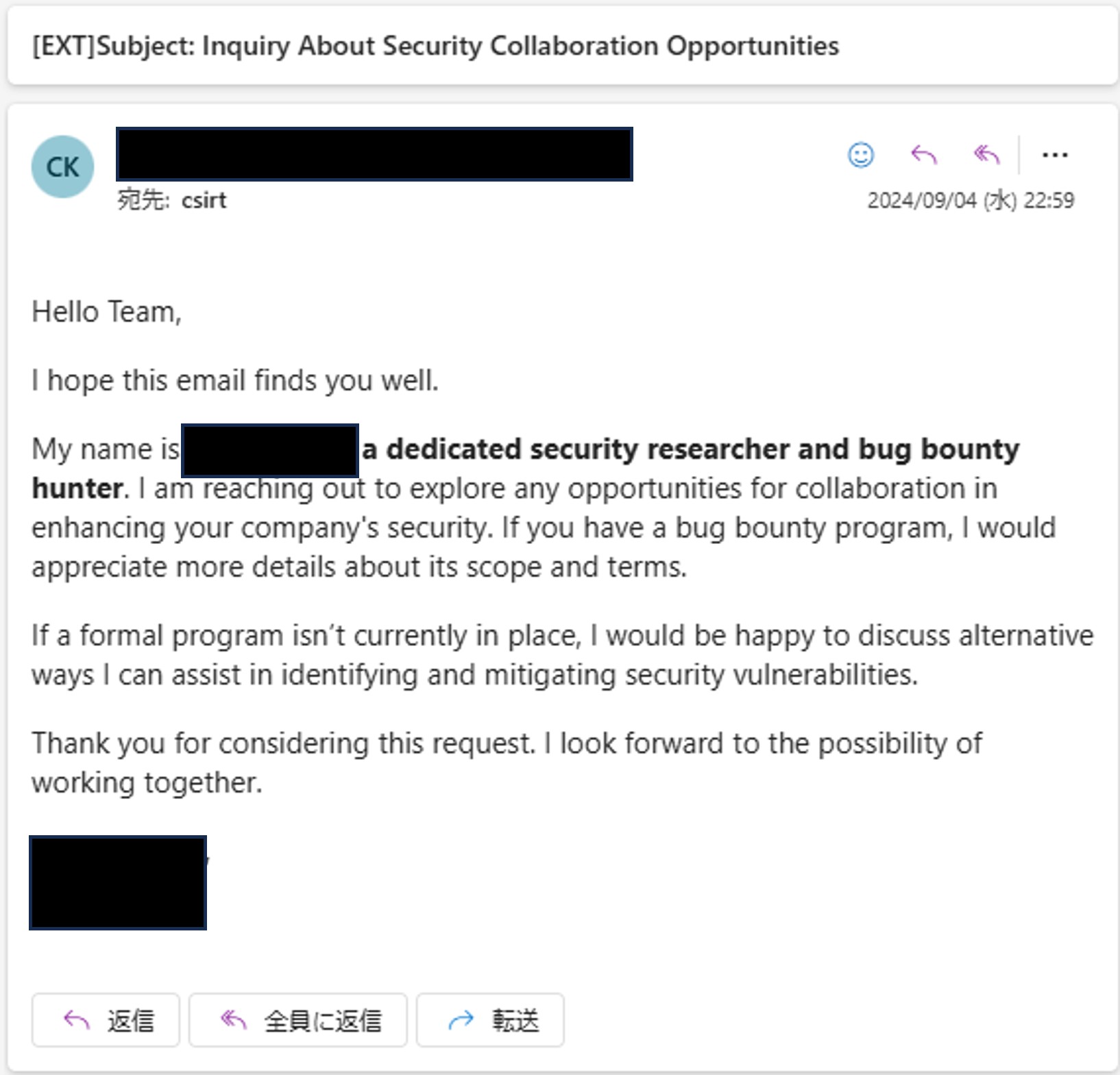
A White Hat Hacker Reported a Vulnerability!
In August 2024, we received a report about a vulnerability in our service. After reviewing the report within our team, we confirmed the issue was real and asked the development team to fix it.
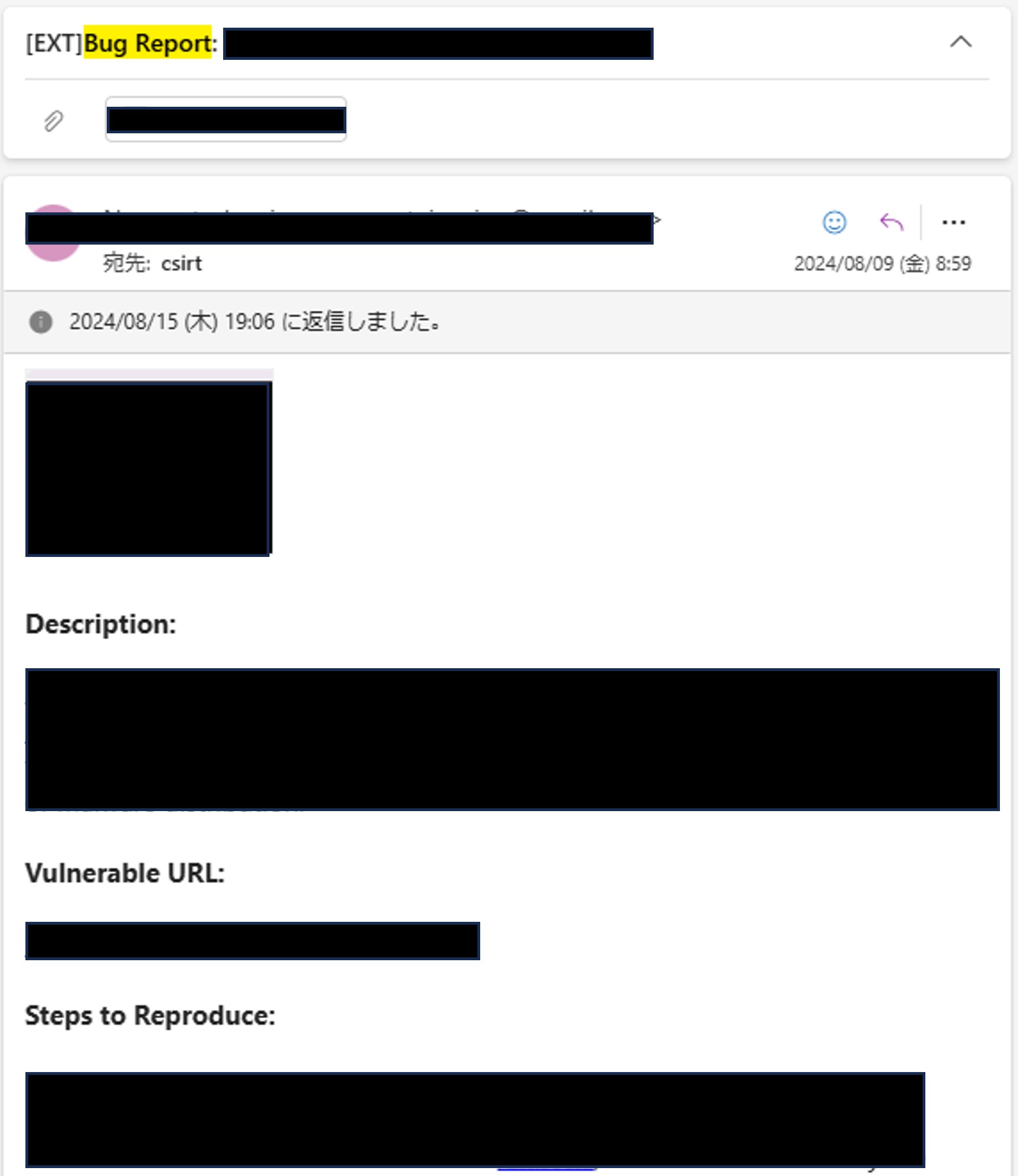
Kaizen for Our VDP
Although we recognized the value of the VDP, we identified several issues. As a result, we started using the VDP service offered by IssueHunt in November 2024.
- Clarify VDP guidelines, including whether a bounty is offered
- Specify which web services and applications are covered
- Provide a report template
As of March 7, 2025, we've received six reports; two of which involved vulnerabilities that required action and have been fixed. Honestly, I'm surprised at the results, which exceeded my expectations.
Our company is featured as a case study on the IssueHunt website. Please have a look if you're interested.
A fresh perspective on boosting security! VDP success story in the car subscription industry (in Japanese)
Our Contribution to the P3NFEST Bug Bounty 2025 Winter
As mentioned above, we do not currently offer a rewards program. However, to evaluate the effectiveness of incentive-based systems and to support students working to secure the future of the internet we’ve decided to contribute some of our services to a student-focused bug bounty program hosted by IssueHunt.
The following services are eligible for bug bounties:
- KINTO Technologies Corporate Site
- KINTO Tech Blog (this website)
The event runs from Monday, February 17, 2025 to Monday, March 31, 2025.
For more information, please visit the event page. We welcome students to take on the challenge. P3NFEST Bug Bounty 2025 Winter
関連記事 | Related Posts
We are hiring!
【ソフトウェアエンジニア(メンバークラス)】共通サービス開発G/東京・大阪・福岡
共通サービス開発グループについてWebサービスやモバイルアプリの開発において、必要となる共通機能=会員プラットフォームや決済プラットフォームなどの企画・開発を手がけるグループです。KINTOの名前が付くサービスやKINTOに関わりのあるサービスを同一のユーザーアカウントに対して提供し、より良いユーザー体験を実現できるよう、様々な共通機能や顧客基盤を構築していくことを目的としています。
【ソフトウェアエンジニア(リーダークラス)】共通サービス開発G/東京・大阪・福岡
共通サービス開発グループについてWebサービスやモバイルアプリの開発において、必要となる共通機能=会員プラットフォームや決済プラットフォームなどの企画・開発を手がけるグループです。KINTOの名前が付くサービスやKINTOに関わりのあるサービスを同一のユーザーアカウントに対して提供し、より良いユーザー体験を実現できるよう、様々な共通機能や顧客基盤を構築していくことを目的としています。


![[Mirror]不確実な事業環境を突破した、成長企業6社独自のエンジニアリング](/assets/banners/thumb1.png)

