Hardening Designers Conference 2025 Event Report

Introduction
Hello! This is Otaka from the Cloud Security Group in KINTO Technologies. On a daily basis, I work on setting up guardrails for our cloud environments and keeping them safe through monitoring and improvements with CSPM and threat detection.
To stay up to date on the latest security trends, I joined the Hardening Designers Conference 2025. Here's my report from the event.
What is the Hardening Project?
The Hardening Project is a competitive event aimed at improving practical cybersecurity skills. Participants run vulnerable systems while defending against, recovering from, and improving them in response to external attacks, building real-world incident response skills in the process. What sets it apart is that it evaluates not only technical skills but also overall incident response capabilities, including teamwork, documentation readiness, and the establishment of an operational system.
The Hardening Designers Conference 2025 that I participated in this time is a hands-on and conference event themed "invisible divide." It served as preparation for the competitive event in October.
Day1 Hands-on Program
In the hands-on session, we experienced an attack technique called "Living off the Land." This technique involves attackers abusing legitimate, built-in tools and functions already in a system to gain access and carry out harmful activities. For example, in a Windows environment, they use PowerShell, WMI, etc. to conduct the attack.
The key is that they use built-in tools and functions, not files brought in from outside. This makes it hard to tell their activities apart from normal operations, and difficult for security tools to detect.
Some of the commands used in the attack were ones I'd relied on back in my days as a system administrator. If a tool or command isn't used in normal operations, disabling it might help. But for those frequently used and hard to turn off, the only real option may be to log and monitor them closely.
The workshop was a real eye-opener, showing just how sophisticated server attacks have become, and how blurred the line is between malicious activities and legitimate operations.
Day2 & 3 Conference Program
On Day 2 and 3, a variety of lightning talks and sessions delved into the theme of "divide" in the context of cybersecurity, with speakers sharing the latest technologies, introducing new initiatives, and hosting lively discussions.
In the security field, there are often "divides" between different stakeholders, and these can become obstacles that hinder Hardening (security fortification) efforts. For example, divides like the following often arise in actual operations:
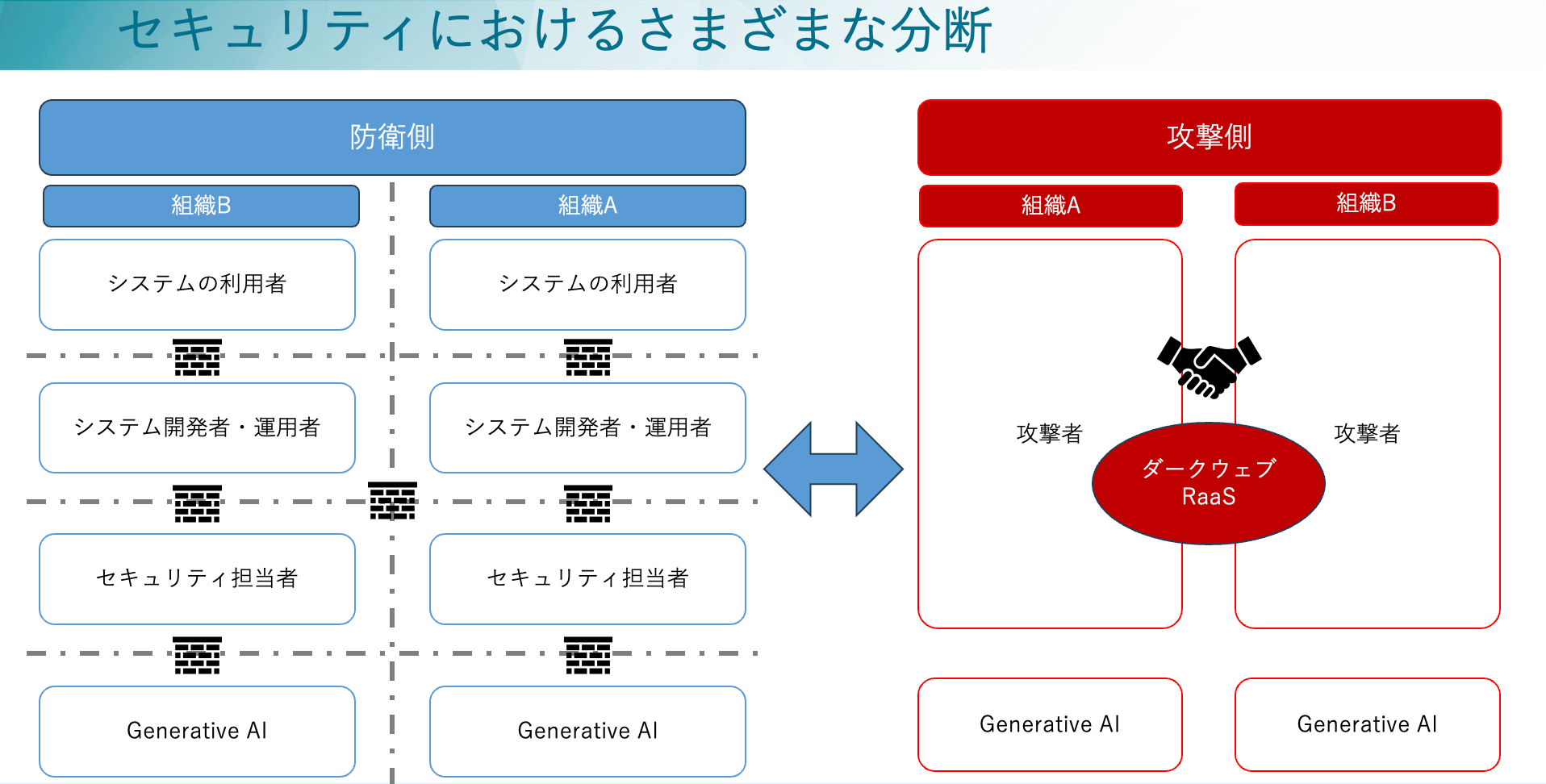
Divide between Development, Operations, and Security
Sometimes, the focus on implementing features and improving operational efficiency can push security to the back seat. For instance, poor password management or weak account controls can create security vulnerabilities. To avoid this, think of security not as a "restriction" but as part of overall "quality," and make sure security requirements are built in from the very start through security-by-design and shift-left practices.
Divide between System Users and Developers/Operators
While system users desire ease of use, they may not fully grasp the importance of security. Engineers, on the other hand, often find themselves caught in the middle, trying to balance user requests for features with the need to keep the system secure. To bridge this gap, it is necessary to educate users and maintain careful communication with them during system development and operation, fostering their understanding of security.
Divide between Rule Makers and Implementers
Security personnel who set rules often draw on a range of guidelines from public bodies and specialist organizations to define ideal baselines and rules. However, for those on the ground such as system development and operations teams, system constraints and operational workload can make it hard to implement them as intended. To put this into practice, it is important to take into account constraints and operational loads and take a flexible approach so that security can be implemented properly.
Divide between Attackers and Defenders
While attackers use technological innovation and teamwork to launch increasingly sophisticated attacks, defenders can end up reacting too slowly because of costs or a lack of understanding among stakeholders. Companies hit by cyberattacks are often reluctant to disclose details, which means valuable knowledge that could prevent similar incidents is not shared in many cases. The defense side would also like to strengthen information sharing and cooperation, but things are not going as smoothly as expected.
Divide between AI and Humans
Efforts to utilize generative AI are spreading in the IT field, from writing program code to upgrading SOC operations. But in reality, AI often can't take security into account without clear and specific instructions, . Generative AI has come a long way, yet there still seems to be a gap between what humans and AI can do. To utilize AI properly, we still need human know-how, like designing effective prompts and setting up guardrails.
When we think about it again, we can see just how many kinds of divides exist. I had never looked at security from this angle before, so this was genuinely insightful.
Overcoming the Divides—KINTO Technologies' Approach
At the Cloud Security Group, our basic policy is "security for business," and we believe that security should accelerate business operations, not slow them down.
We work on security from the following two key angles:
- Preventative guardrails: We provide security preset account environments with the minimum required security settings already implemented before handing them to development teams. This helps support secure design from the very beginning.
- Detective guardrails: We use SOC monitoring with tools such as Sysdig, AWS Security Hub, and Amazon GuardDuty to detect and respond to threats in real time. Through regular Posture management, we also conduct <i>kaizen</i> activities to improve problematic configurations.
Through these security measures and operations, we are working to create an environment where developers can focus on their work with peace of mind, while adhering to our company's security guidelines and ensuring the necessary security. In short, this is an effort to bridge the divide between rule-makers and implementers, and between development, operations, and security teams.
We have also begun taking gradual steps toward AI security (see details here). However, with technology and trends evolving so rapidly, it feels as though we are currently a little on the back foot. Within the company, the use of generative AI in business operations and its implementation into products are advancing actively, and the challenge ahead will be determining how to implement effective controls while overcoming the divide with AI.
Furthermore, we are working to review our mindset toward system development projects at KINTO Technologies, drawing on the IPA's key points for requirement clarification with a house-building analogy as a reference. This is not limited to system construction; from a security perspective as well, it is an effort to be mindful of the divide between system users and engineers, and to foster better relationships and results. For more information about IPA house-building, please see here (in Japanese).
Summary
Through the Hardening Designers Conference 2025, I had the valuable opportunity to learn about security trends from the perspective of divide, something I had not consciously considered before. By looking at my own organization's security through the same lens of divide, I was also able to reaffirm our current initiatives.
Going forward, I hope to continue and refine our efforts to overcome divides and achieve better security.
Lastly
Our Cloud Security Group is looking for people to work with us. We welcome not only those with hands-on experience in cloud security but also those who may not have experience but have a keen interest in the field. Please feel free to contact us.
For additional details, please check here (in Japanese).
関連記事 | Related Posts
We are hiring!
セキュリティエンジニア/サイバーセキュリティ G/東京・名古屋・大阪・福岡
募集ポジションについて本ポジションでは、セキュリティ・プライバシー部/サイバーセキュリティ グループに所属し、当社サービスおよび社内システムのサイバー防御強化に携わっていただきます。SOC運用や脆弱性管理を通じて、企業全体のセキュリティレベルを向上させる重要な役割を担うポジションです。
【クラウドエンジニア】Cloud Infrastructure G/東京・大阪・福岡
KINTO Tech BlogWantedlyストーリーCloud InfrastructureグループについてAWSを主としたクラウドインフラの設計、構築、運用を主に担当しています。

![[Mirror]不確実な事業環境を突破した、成長企業6社独自のエンジニアリング](/assets/banners/thumb1.png)

